Inside Doppelganger – How Russia uses EU companies for its propaganda
For two years, Russia has been spreading its propaganda using cloned websites of Western media outlets. The campaign known as "Doppelganger" hasn’t been stopped yet – despite being sanctioned by the EU and US. A CORRECTIV investigation found that European companies are part of the internet infrastructure that keeps the campaign running.

This article was first published in German on July 11 here.
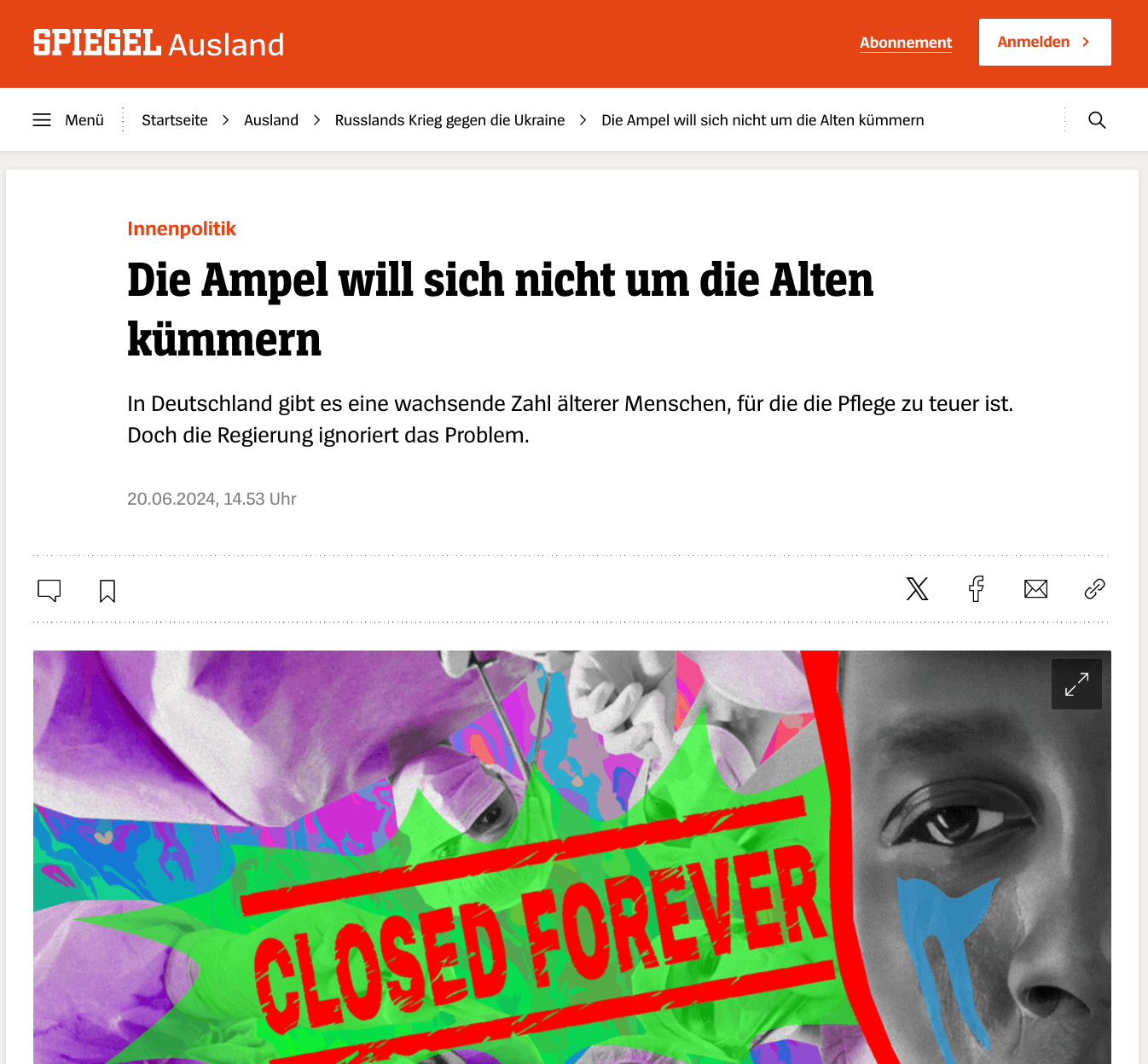
On an afternoon in late June, hundreds of accounts on X began spreading a link to an article by German weekly Der Spiegel. In the report, the author complains about the German government coalition and states that pensions have been frozen to instead finance weapons deliveries for Ukraine. “The government should focus on the welfare of its citizens, not on geopolitical games”, one of the posts reads.
The X-accounts and the Spiegel story are fake. They are part of a Russian propaganda machine that has been pumping out fake news articles and other propaganda content on a near-daily basis for two years.
So far, the campaign, known as “Doppelganger” because of its use of cloned websites, hasn’t been stopped – neither by the EU nor the US, who have sanctioned some of the people behind it.
CORRECTIV can now reveal that Doppelganger partly relies on European and German companies to spread its propaganda, raising questions about how committed European authorities are in fighting Russian disinformation. Based on an analysis by the Swedish NGO Qurium, which specializes in digital forensics, CORRECTIV traced the entire chain of the disinformation campaign – the path that your internet browser takes when you click on a link to one of the fake websites.
Chapter 1: The Beginnings

Moscow, summer 2022. Employees of the public relations firm Social Design Agency are drafting strategies for the mass distribution of content via social networks – as effective and untraceable as possible. These are proposals for a disinformation campaign that will be repeatedly adapted over the following months. The strategy papers make their way to the Kremlin.
In April 2024, the Washington Post reported on a leak from the Russian center of power, which had been passed to the newspaper by a Western intelligence service. Social Design Agency’s proposals were among these documents. One of the suggestions: “short-lived” social-media accounts could be used to disseminate content in order to avoid detection and obscure the origin of misleading information. The documents, which were created between May 2022 and August 2023, were apparently received by the Kremlin. During this period after Russia’s full-scale invasion of Ukraine, the Doppelganger campaign gathered pace.
Since then, links have been automatically distributed on Facebook and X using artificial accounts. These links lead to the campaign’s own propaganda portals, such as “Reliable Recent News”, or to cloned websites of established media such as Le Monde, The Washington Post or Spiegel. Government websites have also been forged in the past, including that of Germany’s interior ministry. The content spread by the campaign often casts Ukraine in a bad light, but it also addresses domestic political issues. Not everything is wrong, but much is distorted.

The EU and the US have sanctioned Social Design Agency and another Russian company called Struktura for their involvement in the Doppelganger campaign. This means that European and American companies aren’t allowed to provide them with services or economic resources – directly or indirectly. In June, the NGO Institute for Strategic Dialogue found evidence for the involvement of another Moscow-based marketing firm called Argon Labs. And there are probably more companies working on the multi-layered campaign.
These companies presumably design concepts, work out ideas and topics and disseminate the results online, such as the supposed Spiegel article.
However, a number of companies that have received very little attention so far are responsible for the technical aspects of the campaign. They ensure that articles like the forged Spiegel story about military aid to Ukraine at the expense of German pensioners remain available online and reach their target audience. The trail of these companies first leads us to the British capital.
Chapter 2: The Evil Empire

London, summer 2023. Fergusson House is a five-storey red-brick building in the center of the city. Well over 5,000 companies are registered here at 124 City Road, many of them shell companies. For around 40 pounds a year, anyone can rent a “virtual office” at the address and register a company from anywhere in the world.
On August 29, 2023, another company is added to this list: TNSecurity Ltd. The company plays an important role in the Doppelganger machinery. According to Qurium’s research, it is home to hundreds of web domains for the propaganda campaign. The links are a disposable product; they are scattered thousands of times in social networks to redirect to the campaign’s content, making TNSecurity one of the gateways to the propaganda network.
The company’s services are also used for criminal activities. TNSecurity is characterized by an “unusually high level of malware activity,” according to a May 2024 report by Canadian IT security company Hyas, which monitors cybercriminal and malicious online activity. “TNSecurity may have been compromised or is intentionally working with cybercriminals,” the report said. Taking this assessment into account, the people behind the company came up with a fitting name for part of their infrastructure: “Evil Empire”.
Why Doppelganger needs thousands of domains
When visiting the fake Spiegel article, the address bar of your internet browser doesn’t show the actual address of Spiegel (spiegel.de) but spiegel.ltd. Doppelganger has been using this domain to distribute fake articles of the German weekly for years.
Like many other Doppelganger addresses, spiegel.ltd has been blocked by Facebook and X. A link to it can no longer be shared on the platforms. The Russian disinformation campaign therefore relies on a sophisticated system to conceal the link’s real target, using redirects via other domains.
It works like this: On X and Facebook, artificial profiles, so-called bots, spread meaningless-sounding links. In the example of the Spiegel article, the link was “hkrfd2.newtrendsboutique.com/l5pn9q”. Sooner or later, the platforms block these links. A constant supply of domains is therefore needed to keep the propaganda machinery running.
TNSecurity was registered in the name of Anastasija Berezina, who was 18 years old at the time and Latvian, according to the British companies register. In reality, she may be from Pskov in north-western Russia, CORRECTIV reporting shows. Whether she really controls TNSecurity is unclear. The company didn’t reply to a request for comment sent to a registered email address. Berezina couldn’t be reached by phone.
Around a dozen British companies were registered in London within a few months in 2023 and 2024 by young people from Russia, Ukraine, or Kazakhstan – often at the same address in London. Some of them are providing services for the campaign. For example, the companies DPKGSoft International and Netshield, which in recent months have been running more and more of the disposable domains that redirect to fake content. In a response to a request for comment, Netshield claimed to have deleted some domains. Other Doppelganger domains hosted by the company remain online.
The companies have another thing in common: They all have a connection to a young St. Petersburg IT company that has made an astonishing rise over the past two years. The analysts at Qurium suspect that it plays a central role in the Doppelganger infrastructure – as a Russian hosting provider with European presence and good connections.
Chapter 3: A rapid rise

Saint Petersburg, summer 2024. Arseniy Penzev is 21 years old and co-founder of Aeza, a company in Saint Petersburg. On his Telegram account, he can be seen at a Russian entrepreneur meetup, or he films himself with his business partner Bosoyan in a hotel in Moscow. His company Aeza presents itself as a modern start-up, its employees live stream on Youtube. Recently, the company visited a Moscow university.
According to Aeza, it now owns around 40,000 servers. Qurium estimates that the company owns IP addresses worth around 2.4 million euros. With Aeza, Penzev has made it into the premier league of Russian web hosts. And he seems to be surprised about this success.
Penzev started working on hosting projects as a teenager. Things seemed to get serious in 2021 when Penzev and his business partner Bosojan set up the hosting company MSKHost. The project came to an abrupt end in September of the same year. According to Penzev, the service was hacked and he lost his business overnight. Former customers, on the other hand, suspect that they were cheated, that the hack never took place but was a so-called exit scam. This makes the rise that followed all the more surprising.
In his blog entry, Penzev explains how he got unexpected help after MSKHost crashed. Suddenly, strangers appeared in Moscow with “crazy iron”, meaning the fast server hardware that his team dreamed of having. These strangers didn’t know who to trust with the technology and were willing to cooperate in the form of a new hosting provider, Penzev says, without explaining who they were. Aeza didn’t respond to a detailed list of questions about this and other aspects.
Similar to its predecessor company MSKHost, Aeza presumably allows criminals to operate on its servers. It advertises its services in underground darknet forums, for example. According to experts, Aeza’s offer to use servers by the hour is also a hidden invitation to cyber criminals.
It is doubtful that a rise like Aeza’s is possible in today’s Russia without the blessing of the authorities. One may imagine a kind of trade: the authorities allow Aeza to operate, and in return the company makes its international and widespread structure available for the distribution of propaganda. Experts have long suspected that there could be a cooperation between such hosting companies and Russian intelligence services.
According to Qurium’s analysis, Aeza forms the nucleus of a network of hosting companies in Russia and the UK, all of which are closely linked. Some are direct or hidden offshoots of Aeza, such as Aeza International Ltd or H2Nexus Ltd, while others have overlapping entries in internet registers, such as Waicore or Aeza.
At TNSecurity, where the throwaway domain that redirected to the fake Spiegel site was based, Aeza is partly upstream in the data traffic. In its report, Qurium describes the company as the “center of the Doppelganger ecosystem”. In short: Aeza is of central importance for the distribution of the campaign’s content.
Before you even get to see the fake Spiegel website, the data makes another stop at a major internet hub, for example in the German city Frankfurt am Main.
Chapter 4: The Gateway to the World

Langen, June 2024. Joseph Hofmann sits in his office on the second floor of a building complex in the industrial area of Langen, 20 minutes by train south of Frankfurt am Main. The room is bare and far too big for one person. There is a sofa in the corner and a few tables in the middle, where Hofmann has set up two screens. From here, he manages his IT company Aurologic and his own data center, Tornado.
The analysts at Qurium have established that some data traffic from TNSecurity and other companies in Aeza’s sphere of influence runs via Aurologic, meaning they use its connection to global internet providers. This also applies to the Doppelganger domains that lead to the fake news sites.
This is an explosive discovery, as it would mean that a German company is providing its services – whether knowingly or not – for a disinformation campaign whose perpetrators have been sanctioned by the EU.
Hofmann says he only knows a few of the dozen or so companies from Aeza’s cosmos that, according to Qurium’s research, had a connection to Aurologic in the past. In an interview with CORRECTIV, he didn’t say how many are direct customers and who in turn may be a client of a client. Such nested structures are common practice in the IT industry. He recalls that Aeza once had a server in his data center.
TNSecurity also appears to use the services of Aurologic. According to information by Spamhaus, an organization that monitors malicious internet activity, Aurologic didn’t respond to dozens of abuse reports in connection with TNSecurity. Reports like these inform hosting providers, when customers may be abusing their networks. In these cases, they were about the spread of malware and phishing attacks via Aurologic’s networks. At the meeting, he said that the company would respond to such reports if there was sufficient evidence.
In an email following publication of this story Hofmann wrote that Aurologic contacted Spamhaus many times, but the reports in question weren’t withdrawn despite his requests.
Requests from authorities are part of the business, he says during the meeting in Langen. The allegations regarding Doppelganger are new to him, he claims: “We are not aware of any customer supporting the campaign.” He adds that he isn’t allowed to scan his networks for such content – or even look into his customers’ data storage.
And yet, he is curious. We show him the link that leads to the fake Spiegel article. Hofmann types the address into the command line of his computer to trace the traffic. When the result appears, he is surprised. “Oh, that actually leads to us,” he says.
But that doesn’t prove anything for him. “The authorities have to contact us,” he says, wondering why they haven’t done so yet. “If there are hard facts, we will deal with them.” He formulates his dilemma: “I can kick everyone out, but then at some point I won’t make any sales.” That is why he waits for official mail.
According to CORRECTIV reporting, the Qurium analysis has been circulating among some European authorities for weeks. Some companies named in the report were even known beforehand. So why hasn’t Doppelganger been stopped yet?
The chain of those involved in the disinformation machine doesn’t end in Frankfurt am Main. The data query that you as a reader trigger by clicking on the link to the supposed Spiegel article is ultimately sent back to the browser – via a domain redirection triggered by TNSecurity via the Aurologic infrastructure in Germany. You are then forwarded to the next two stages.
Chapter 5: From Europe to Asia

Tuusula, June 2024. Half an hour’s drive north of the Finnish capital Helsinki, several rows of buildings are spread across a 150,000 square meter site. In the low-rise buildings, under pointed roofs, shielded by a wire mesh fence, machines rattle. This is where a Finnish subsidiary of German hosting giant Hetzner built a large data center six years ago. Somewhere here, on one of the servers, four domains are operated by a customer of Hetzner Finland Oy. They are the bottleneck of the Doppelganger campaign.
A multi-level forwarding mechanism is designed to protect the core of the campaign. In the first stage, there are thousands of random domains that are posted on X and Facebook. In the second stage, the number of domains is reduced to about a tenth. These in turn lead to the third stage – with only four domains left, which then lead to the actual destination.
We have explained the process in this illustration:
This is the core tactic of the Doppelganger campaign – and it isn’t new at all. The same redirection methods are used in phishing campaigns and other malicious activities, according to Spamhaus, the organization that monitors malicious internet activity and which CORRECTIV asked for an assessment. Internet fraudsters use this tactic to prevent valuable infrastructure components such as the “real” domains or servers from receiving too much attention. The further the forwarding chain progresses, the more static the domains and IP addresses involved usually become, according to the experts at Spamhaus.
This is also the case for Doppelganger: according to Qurium’s analysis, the domains in the second level are mainly run by two companies: Liber Systems from the UK and BL Networks from the US. They are only used for redirection. A law firm working for Liber Systems told the Czech portal Investigace, which worked on this investigation with CORRECTIV, that the company only offers a so-called virtual private server service and is otherwise “not involved in the business of its customers”.
Then comes the third stage: While you wait for the supposed Spiegel article to appear in your browser, your device calls up one of the following four domains: cheekss.click, ggspace.space, gooddefr.com or sdgqaef.site. Software installed there, called Keitaro, then recognizes where you are located. Only if you are visiting the website from Germany will you be directed to the last stage, the actual target domain spiegel.ltd, the fake news site. Otherwise, you will be directed to a random website.
All visitors to the thousands of domains in the preliminary stages are channeled through these four addresses. They all go through Hetzner in Finland. Blocking this one customer would stop the whole machinery – but probably only until the data flow is redirected.
It is European companies that make the crucial final stage possible in the first place: The Keitaro software also comes from a European company, the Estonian Apliteni OU. As with the German company Aurologic, the authorities would have a lever here to take action against the campaign. Sanctions have been imposed on some of the people behind it and European companies are therefore not allowed to provide resources to them, either directly or indirectly. On top of that, criminal activity seemingly also takes place via parts of the same infrastructure.
At the last stage of the redirection chain, where the fake news sites are actually operated, European authorities most likely have little to no influence: domains such as spiegel.ltd, sueddeutsche.ltd or washingtonpost.pm are hosted with the Malaysian-based company Shinjiru Technology. Some other websites are located in Singapore with a subsidiary of the Lithuanian hosting-giant Hostinger. Shinjiru didn’t answer questions regarding the hosted Doppelganger websites. Hostinger stated that it saw no signs that the pages were located on its servers, but requested further information.
Hetzner replied to a request for comment that the customer in question wasn’t sanctioned and that it wasn’t aware of any possible connections to a sanctioned person or organization. The company said it had no knowledge of the incident and would “take appropriate measures to prevent further future infringements via our servers” should the allegations prove to be true. The Estonian company Apliteni did not answer questions about its role.
On the government side, individual ministries and authorities in different EU countries, such as in Finland, sometimes referred to each other when answering questions about possible sanctions violations. The Estonian Consumer Protection and Technical Regulation Authority, which is responsible for enforcing sanctions, said that it hadn’t yet taken a closer look at the structure behind the campaign. “The technical nuances require further investigation on our part,” said a spokeswoman.
According to CORRECTIV reporting, an early version of the Qurium report had already been circulating among government officials since spring of this year in at least two EU countries, including the German foreign and interior ministries. However, the information apparently hasn’t yet been used to put a stop to the campaign.
Chapter 6: The Distribution

Moscow, June 2024. We don’t know whether Alina Malinina works for the PR firm Social Design Agency, Struktura, Argon Labs or another company. Nor is it clear whether this is her real name. But thanks to a small mistake, we know that she is part of a team that distributes content for Doppelganger. A moment of carelessness offers a glimpse into the human level behind this highly automated disinformation machinery.
Instead of a cropped image, someone from Malinina’s team uploaded a full screenshot in a Facebook ad for Doppelganger. It shows a chat on the Russian platform VK with several employees. In the center is the actual preview image, posted by a certain Alina Malinina. It was probably intended to illustrate a French Doppelganger article accusing Ukraine of wasting money.
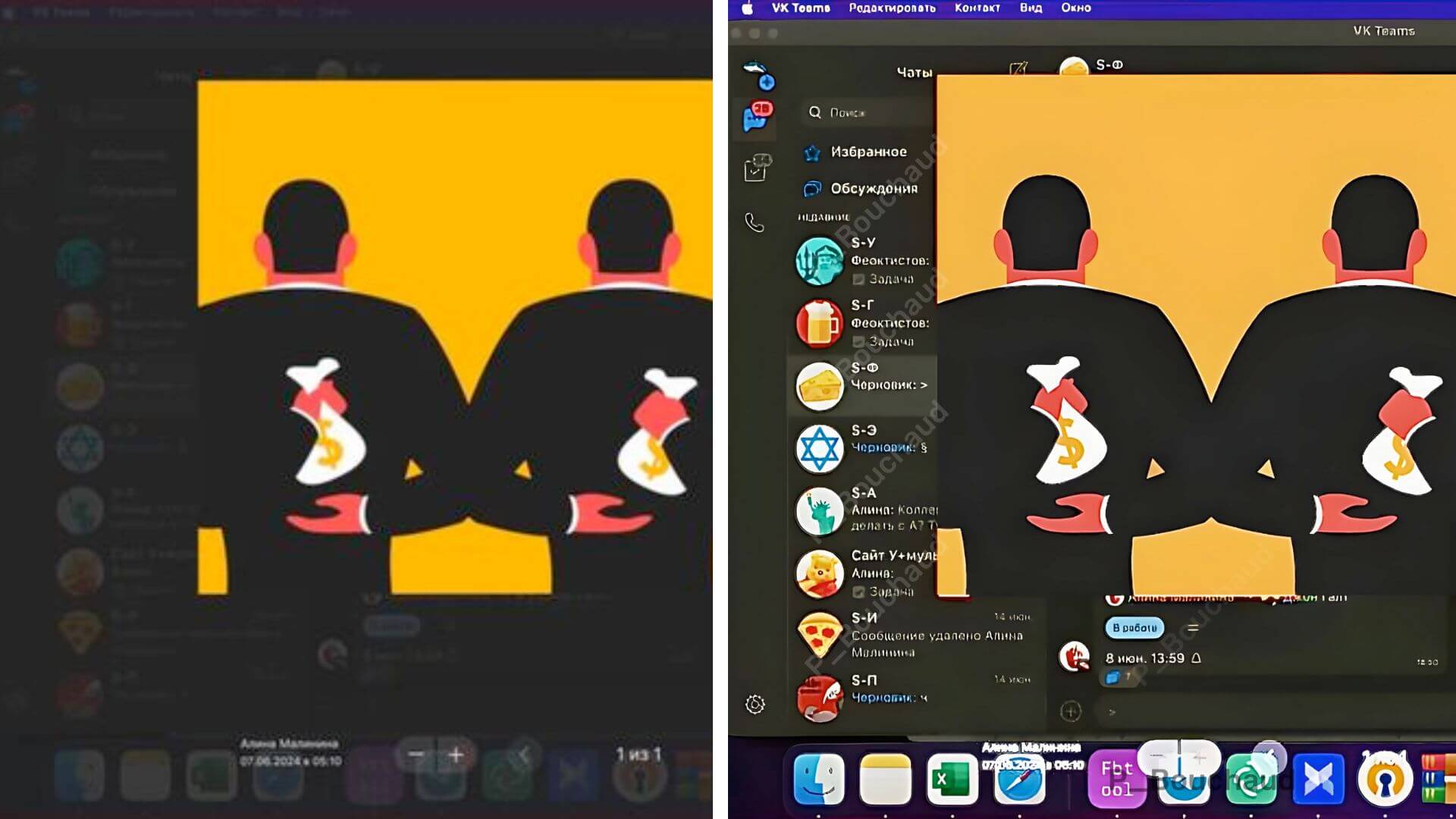
This error was discovered by IT researcher Paul Bouchaud. With a few tricks, symbols for individual chats become visible: a Statue of Liberty for the US, a pizza for Italy, a beer mug for Germany. You can see that someone has posted the link to a fake article on the website leparisien.wf and defined tasks. It is possible that the fake Spiegel article from our example was also edited this way.
Everything seems to be going according to plan for the Doppelganger campaign on this day. Alina Malinina replies: “check”. A few days later, the campaign’s bots spread fake articles from Le Parisien and other media. Even after more than two years, the propaganda keeps going – neither politicians nor platforms have been able to stop it.
This investigation was carried out in cooperation with Investigace.cz and VSquare.
Editing: Anette Dowideit, Alice Echtermann, Sarah Thust
Fact-Checking: Stella Hesch
Production: Alice Echtermann
Design: Mohamed Anwar, Ivo Mayr
Translation: Max Bernhard
How we reported this story:
For our investigation, we worked together with the Swedish NGO Qurium, which provided us with a preliminary version of its now public analysis of the Doppelganger infrastructure. CORRECTIV then spent several weeks researching the companies and individuals involved and conducted numerous interviews with experts, authorities and other parties. We worked on the research together with Investigace.cz and VSquare, who took a closer look at the companies involved in the Czech Republic in particular. Qurium’s analysis is based in part on data provided by Antibot4Navalny, an anonymous volunteer group that tracks Russian disinformation on X.



