Doppelganger: CORRECTIV investigations bring Russian propaganda campaign to a halt
The spread of fake websites by the Russian disinformation campaign Doppelganger has largely been stopped. The people behind the campaign had been using a Ukrainian service provider – which quickly blocked the Russian customer after a CORRECTIV inquiry. Doppelganger’s digital footprints meanwhile lead directly to the Ministry of Defense in Moscow.

What this investigation reveals:
- For years, Doppelganger circulated links to numerous fake websites via social media networks like Facebook and X. To avoid being detected by these platforms, the campaign organisers used a Ukrainian service provider. Following an inquiry from CORRECTIV, the service provider blocked Doppelganger in October, severely disrupting the campaign’s operations. Since then, most of the links on X have become inaccessible.
- After the U.S. Department of Justice shut down several of the campaign’s websites in September, Doppelganger registered new domains through a German company. Following further inquiries by CORRECTIV, this German company also took down the sites, making Doppelganger’s key portals, such as “Reliable Recent News”, unavailable since November 7.
- CORRECTIV also uncovered independent evidence of Russian state actors’ involvement in the campaign. Access to several technical services was traced to an IP address linked to the Russian Ministry of Defense.
The bots on X are still relentlessly active. “Zelensky needs to end the war and start peace negotiations with Russians,” writes Wendy Ramos in Ukrainian, adding a sombre collage with the caption, “We’re giving up one area after another.” Katie Garcia criticises the U.S. Democrats in English, accusing them of “playing the good guys while lining their own pockets.” William Hamilton complains in German about the “vast sums” the German government is spending on the Ukraine war despite inflation.
These posts are all part of the Russian propaganda campaign Doppelganger, aimed at swaying Western opinion against Ukraine. According to statistics that have most likely been inflated, some of these posts have been shared hundreds of times. Originally, the links in these posts led to manipulative articles. However, by early November, most links simply resulted in an error message: “404 Not Found” or “Page Not Found.”
This disruption is due to recent investigations by CORRECTIV and the IT forensics organisation Qurium. After more than two years, the disinformation campaign has currently lost much of its influence.
This article was first published in German on November 13 here.
The infrastructure of the Russian propaganda campaign Doppelganger gradually crumbled
This is how Doppelganger functions: it sets up artificial accounts on social networks, which post links to Doppelganger’s own ‘news’ portals or to replicas of reputable German news sites such as Spiegel or Süddeutsche Zeitung. These deceptively real cloned news sites contain anti-Ukrainian and anti-Western articles.
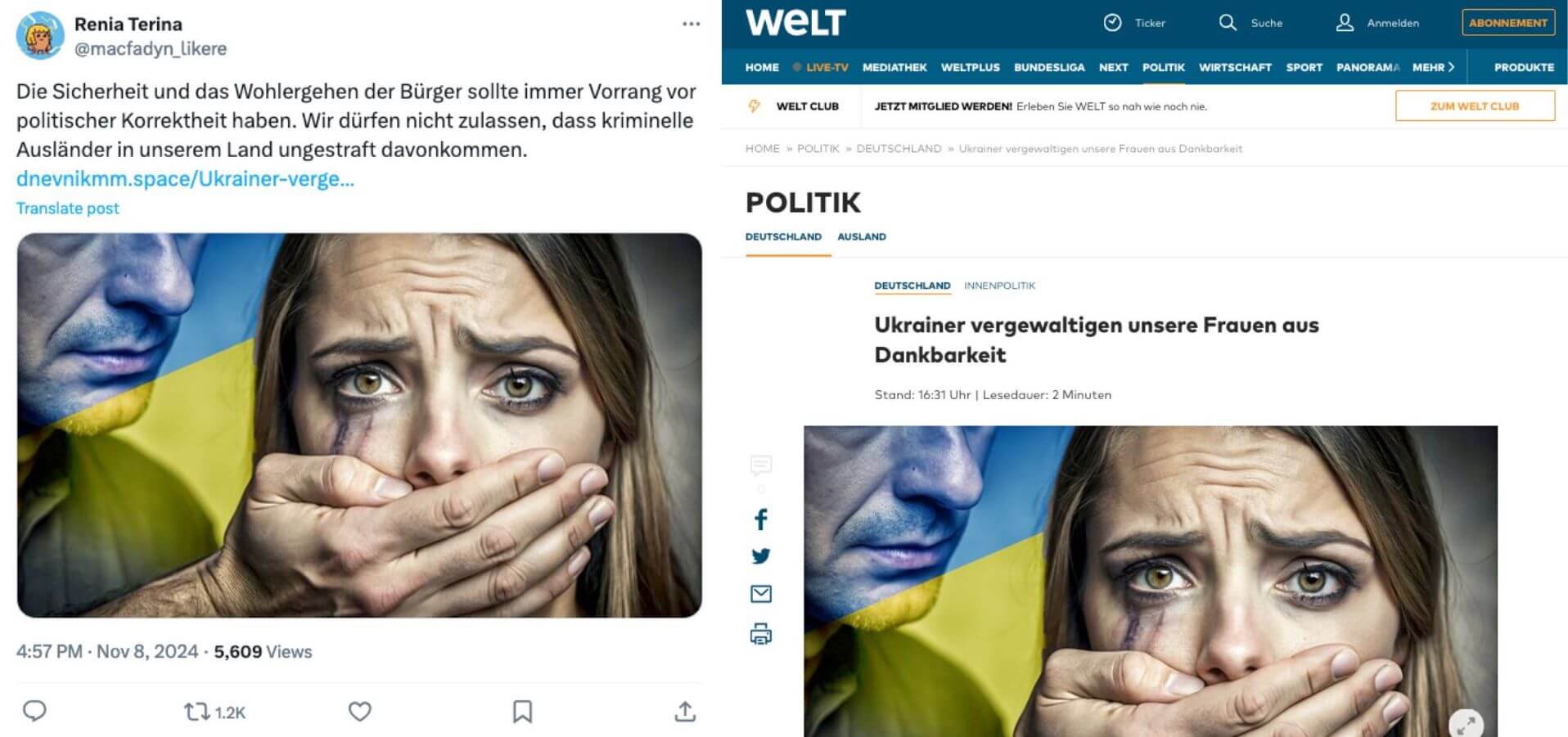
Since CORRECTIV and Qurium revealed this summer that Doppelganger was using the services of European IT companies, these companies have gradually withdrawn their services from the propaganda campaign. The Russian entities behind the campaign – two companies called Struktura and Social Design Agency – have been sanctioned by the EU since mid-2023, but to little effect.
Most Western service providers claimed not to have known who they were serving as a client. For example, Doppelganger used servers operated by the German hosting company Hetzner for many months. The company closed Doppelganger’s customer accounts after our publication this summer.
The Estonian software company Apliteni also confirmed to CORRECTIV that its product, a redirection software called Keitaro, had been used by Doppelganger without its knowledge. Apliteni revoked the relevant licences. “We are actively working to prevent such misuse of our product in the future,” said company CEO Artur Sabirov. The Keitaro software was crucial to the campaign, allowing propaganda articles to be targeted at specific audiences in the intended countries. In the past, Russia had been increasingly focussing attention on countries like France and Israel, and more recently Doppelganger shifted its attention to the United States, particularly in light of the elections.
Fake news websites are concealed using a mechanism commonly associated with cybercriminals
To prevent the links to Doppelganger’s websites from being blocked by platforms like X or Meta, the campaign’s architects employed a mechanism popular with cybercriminals.
Typically, websites can easily be identified by their domains – for instance, Spiegel’s is always spiegel.de. Doppelganger created fake websites with similar domains, such as spiegel.ltd. Links to these fake websites were eventually blocked on Facebook. To circumvent this, the propagandists temporarily borrowed dozens of inconspicuous, disposable domains. Examples from the past include climzenante.shop and lowlementor.shop. These domains are then distributed across social networks, redirecting users to the actual Doppelganger website. This involves a number of technical processes to ensure that, for instance, a certain page is only shown to people in Germany. Meanwhile, X’s content moderation team only sees an innocuous website and does not detect it as a fake.
This practice is known in the industry as “cloaking.” Various types of scams, such as cryptocurrency or dating fraud, also use this technique to promote deceptive ads.
Deliberately circumventing the moderation mechanisms of these major platforms is in itself a violation of their terms of service. In 2020, Meta, the parent company of Facebook, took a cloaking service provider to court over the matter. However, the company declined to answer how it is currently tackling cloaking. “Fraudulent content is not tolerated on our platforms. However, fraudsters continuously adapt and develop new methods to bypass our systems – Doppelganger is one such example,” a company spokesperson said. X did not respond to a request for comment.
Cloaking service’s trail leads to southern Ukraine
Research by Qurium, based on data by the initiative Antibot4Navalny, found that Doppelganger has been relying on a cloaking service called Kehr since at least May 2023. Our investigation revealed that at least 147 disposable domains, such as radilwanised.shop and shuanse.shop were used by Doppelganger via Kehr to spread links on social networks.
Since cloaking services operate in a legal grey area, and often tolerate use by internet fraudsters, the operators of such services usually try to remain hidden. Kehr is no different– while the service advertises primarily on Russian-language forums, it does not list any responsible parties on its website.
However, CORRECTIV managed to identify those responsible. The digital trail led to southern Ukraine – the very country against which Russia is conducting the campaign.
At the end of October, we requested a comment from the operator of Kehr. He was surprised. “I am extremely opposed to any propaganda against my country,” he told CORRECTIV. The man, who fears for his safety and whose name we will therefore not disclose, immediately informed us of the action he had taken: “The user was blocked, and their service was shut down.” The effect was immediate: since the end of October, most of Doppelganger’s links on X no longer work.
Whenever a service provider blocks Doppelganger, the campaign looks for an alternative. According to Qurium’s research, one has already been found for Kehr. However, the links currently being spread on X still lead nowhere.
German company also reacts after CORRECTIV’s inquiry
However, it’s not just the redirection mechanism that has been disrupted, it’s also the propaganda sites the links should lead to. In early September of this year, the U.S. Department of Justice seized 32 websites linked to the campaign. They included the domains of the Doppelganger portals “Reliable Recent News” and “Tribunal Ukraine.” Since then, these sites – as well as several media clones like faz.ltd – have displayed an FBI notice.
The Russian campaign then adapted and registered new, similar domains for these websites with a different service provider. For example, “Reliable Recent News” could then be found under rrn.news instead of rrn.media. Despite sanctions, the Russian propagandists chose a German company, 1API GmbH from Saarland. The new websites were accessible until early November.
We confronted the company 1API GmbH and sent them 28 addresses linked to Doppelganger sites. A company representative responded that the domains had been “blocked after a brief review due to violations of our terms of service.” At the time of publication, a large proportion of the propaganda portals are no longer accessible.
Accounts accessed by Russian Ministry of Defence
According to CORRECTIV information, both the customer accounts blocked by Hetzner over the summer and the Apliteni and Kehr servers were accessed by, among others, an IP address belonging to the Russian telecommunications provider Voentelekom. Several Western governments have already sanctioned this company. Voentelekom was founded by the Russian government and operates under the Russian Ministry of Defense, serving as its primary telecommunications provider.
This is further confirmation that the Russian state is directly involved in the campaign. This connection had largely only been established by intelligence agencies like the FBI, until now. Moreover, internal documents of the Russian presidential administration revealed the involvement of its head, Sergey Kiriyenko, in the planning of the campaign.
The offices of the two Russian media companies, Social Design Agency and Struktura, which are responsible for executing the campaign, are within walking distance of the Russian Ministry of Defense’s headquarters in central Moscow. Our investigation now shows that either the companies share an internet connection with the Ministry, or a Ministry employee directly accessed the campaign’s accounts.
The Doppelganger propaganda network has gradually been stripped of its technical foundation – the fake news articles now reach hardly anybody. And as a result, they are rendered powerless.
This investigation was carried out in collaboration with Qurium and with the help of data provided by Antibot4Navalny.
Text and reporting: Alexej Hock, Sarah Thust, Max Bernhard
Production and fact-checking: Alice Echtermann
Editing: Alice Echtermann, Matthias Bau
Design: Ivo Mayr
Graphic design: Laila Shahin
Translation: Ellie Norman


