Hacks and Propaganda: Meet the Two Brothers Bringing Russia’s Cyber War to Europe
Since its full-scale invasion of Ukraine, Russia has stepped up disinformation and hacking campaigns against the West. A CORRECTIV investigation shows how two brothers from Moldova provide the technology needed for these attacks.

This article was first published in German on May 16 here.
The Neculiti brothers share a passion for BMWs and traveling. Ivan, the older one, frequently reviews restaurants in cities like Tokyo and Paris on Google. In a drag race in his home country of Moldova, Ivan came second place last year with photos showing him smiling on the podium. Yuri, the younger brother, shows off his luxurious life on Instagram. In photos on his account, he is overlooking the cliffs of Madeira, a lush Portuguese island off the coast of North Africa, or posing in front of a gold-green sports car.
With their web-hosting services, the two Moldovan brothers seem to have built significant wealth. The trail of their business activities, however, leads to the dark side of the industry: the Neculitis’ services are used by an elaborate Russian disinformation campaign, as well as pro-Russian hackers who frequently target Europe’s digital infrastructure, this investigation shows. Since its full-scale invasion of Ukraine, Russia is waging its hybrid war against the West with renewed intensity. and middlemen, such as the Neculitis, appear to make money in the process by providing the necessary infrastructure.
CORRECTIV’s investigation traces their business network from the Seychelles, via a shell company in London to a data center in the Netherlands. And reveals how these attacks are being carried out from within the EU. How well equipped is the bloc against Russia’s digital assault and how effective are sanctions against the Kremlin’s influence campaigns if they are allowed to remain online indefinitely?
Glossary of relevant terms
Bots are computer programs that automatically perform repetitive tasks. The term can be applied to various areas. In social networks, bots usually mean artificial accounts. In the context of DDoS attacks, botnets, i.e. networks of devices, are used for attacks.
A data center is a physical location where servers and other data processing equipment are kept. These can be used by a single company or shared. If the center belongs to an operating company which makes the physical infrastructure available to other companies for a fee, this is known as colocation. In this case, customers are often smaller companies that cannot afford expensive maintenance.
Disinformation is the targeted dissemination of false or misleading information. It can originate from state or non-state actors. Russia uses disinformation as part of its hybrid warfare.
DDoS attacks are aimed at overwhelming a system. For example, a website is accessed in a coordinated manner by a large number of users or computers at the same time (“distributed”) and thereby paralyzed (“denial of service”). In most cases, such attacks do not cause any major damage.
In modern conflicts, hybrid warfare refers to the combination of different methods to achieve specific objectives. In addition to traditional military operations, this can include propaganda, hacking campaigns or economic pressure.
Servers are computers that store data or programs and are connected to a network. Other devices on this network can access them and retrieve information. For example, websites are stored on servers and accessed by users via the internet. However, cyber attacks can also be launched and coordinated via servers.
VPS stands for virtual private server. Hosting companies sometimes divide the resources of a single physical server that has more power and memory than is necessary for many customers into several virtual servers.
Web hosting, or simply hosting, is the provision of storage space on a server. The most important service provided by a host is the accommodation of websites and associated files.
The Neculitis: Two Brothers From Transnistria Target the Russian Market
Ivan Neculiti stems from Bender, a small town in the pro-Russian breakaway region Transnistria, which proclaimed its own state in 1990 but isn’t recognized internationally and has remained firmly within the Kremlin’s orbit. At first glance, there is little to be found online about Ivan and his past. The 31-year-old always uses the same picture in profiles on social media, showing him in a white t-shirt with sunglasses. At a young age, he started to make money on the internet, working for a movie website among other things, he said in a promotional interview.
Today Ivan owns a company, PQ Hosting, based in the Moldovan capital Chișinău. PQ stands for perfect quality. He describes his story like that of the American dream: He risked a lot, worked his way up, and ultimately earned success. His hosting service now offers servers in 38 countries, according to itswebsite. The car race in his home country, in which Ivan came second, was sponsored by PQ Hosting. His brother Yuri, who owns a small share of the company, also gave an interview there as a race-car driver and BMW fan.

On the surface, Ivan offers low prices, a wide range of locations and a variety of payment methods. But there are other things that make his services attractive to a very specific clientele. Despite international sanctions, PQ Hosting is focusing on Russia as a market. A year after Russia’s full-scale invasion of Ukraine, Ivan said in an interview: “As far as the sanctions policy in the world is concerned, you can rent a server in Norway, for example, and use it to access the internet. Then you are a Norwegian to the online world and have nothing to do with sanctions.” The sanctions on Russia imposed boosted demand for locations in different countries, he added. In other words, Russians can run their activities via the Neculitis’ servers in the EU and thereby circumvent any sanctions-related blocks.
In response to a request for comment, Neculiti said that activities in Russia had been reduced “since the beginning of the conflict in Ukraine.”
At the time of writing this article, however, PQ Hosting was still offering its customers a large variety of Russian payment services.
A Shell Company in London
In 2022, Ivan Neculiti founded Stark Industries Solutions Limited – the company name seems to have been inspired by the “Iron Man” movie franchise. The main character, a superhero who is also a tech genius and billionaire, runs a business with a similar name. Neculiti’s web hosting service offers so-called virtual private servers, meaning parts of larger physical servers that can be rented for specific purposes. The cheapest rate, using a server based in the Netherlands, is 5.99 euros a month.
On paper, Stark Industries Solutions is currently controlled by Ivan’s brother Yuri. CORRECTIV’s investigation suggests that it is merely a shell corporation for PQ Hosting.

In one of his promo interviews Ivan explains what the purpose of the UK company is: “At the moment, our IP addresses no longer show that they belong to PQ Hosting. There is a different, neutral name.” The UK company is not involved in payment transactions at all, he says, but is merely there to facilitate business. In other words, anyone doing business with Stark Industries Solutions is actually doing business with PQ Hosting, except that outsiders won’t immediately see that.
Using this corporate structure, the Neculiti brothers operate computers in a modern data center near Amsterdam. There, the Neculitis’ services are used by hacker groups and criminals. To this day, pro-Russian cyber activists use these servers in the Netherlands to launch their attacks against the digital infrastructure of Ukraine and its allies. And companies with ties to the Russian state bypass EU sanctions to spread propaganda across the bloc – with the help of Stark Industries Solutions.
“Doppelganger”: A Russian Disinformation Campaign
In the summer of 2023, the French government reported the discovery of a digital influence campaign with the “involvement of Russian or Russian-speaking individuals and several Russian companies”. At the heart of the campaign: “Recent Reliable News” (RRN), a supposed news website which is actually used as a platform to disseminate pro-Russian propaganda.
RRN’s articles and videos stoke fears of economic collapse in Western countries or predict the demise of NATO – and they agitate against support for Ukraine. “Habeck has lost touch with reality,” reads one headline referring to the German vice chancellor, “NATO dies at 75” another. RRN links were repeatedly shared by well-known disseminators of pro-Russian disinformation in Germany, such as Alina Lipp.
RRN is part of a wider campaign, also known as “doppelganger”, which has been spreading links to propaganda blogs and forged European media and government websites since 2022. CORRECTIV reported previously, how “doppelganger” is active on Facebook and X to this day.
One month after the French government’s report, the EU placed the alleged key actors behind RRN on its sanctions list: the Russian companies “Structura” and “Social Design Agency” and their directors. The companies are “closely linked to Russian political power” and the campaign aimed at “distorting information and disseminating propaganda in support of Russia’s war of aggression against Ukraine”, the EU said.
Sanctions against Russian companies and individuals are intended to ensure that no European company does business with them – directly or indirectly. The propaganda websites are supposed to disappear from the web. However, the example of RRN shows how flawed the European sanctions system is. RRN remains online and spreads its manipulative content – in ten languages, including English and German.
Not only that but according to CORRECTIV’s investigation, until recently the website was running on computers in the heart of the EU, in the Netherlands, – on servers owned by Ivan and Yuri Neculiti. Responding to questions by CORRECTIV, Ivan Neculiti said the associated account and server had been blocked. “We deeply regret only now learning that one of our customers is a sanctioned portal,” he said in an emailed response. However, RRN can still be accessed via the Neculitis’ servers – only now the hosting provider is cloaked behind a well-known privacy service that makes it harder to trace the infrastructure behind the website.
In the Midst of a Hybrid War
Politicians and experts speak of a “hybrid war” that Russia is waging: Tanks and soldiers on the battlefield. Sabotage and covert operations against critical infrastructure. False information and propaganda in the information space. Hacks and DDoS attacks against government institutions and private companies.
Aside from tanks and soldiers on the ground – Russia has employed these other methods of warfare not only against Ukraine but also the country’s Western allies.
In the summer of 2023, Swiss authorities registered a wave of DDoS attacks that lasted several days. The websites of the Swiss Federal Railways, airports, various authorities and larger municipalities in German-speaking countries were bombarded with requests in order to render them useless. The apparent reason for these attacks were Switzerland’s adoption of sanctions against Russia, arms exports to Ukraine and a planned speech by Volodymyr Selenskyj to the Swiss parliament. Two days after the Ukrainian president’s visit was announced, the Swiss Federal Office for Cybersecurity (BACS) registered the first DDoS attack.
According to the Swiss cyber authority, pro-Russian hacktivists, members of the NoName057(16) group, were behind the attack: The group operates using a kind of competition: the people in charge select targets and announce their planned attacks on public Telegram channels. Thousands of volunteer participants then descend on the advertised targets using ready-made programs provided by the hacking group. Those carrying out the largest number of attacks get a prize: around 800 euros. Aside from that, the group also uses botnets, networks of infected computers, for its campaigns.
Other countries such as Germany, Estonia, Denmark and Slovakia have reportedly also been caught in the crosshairs of NoName057(16).
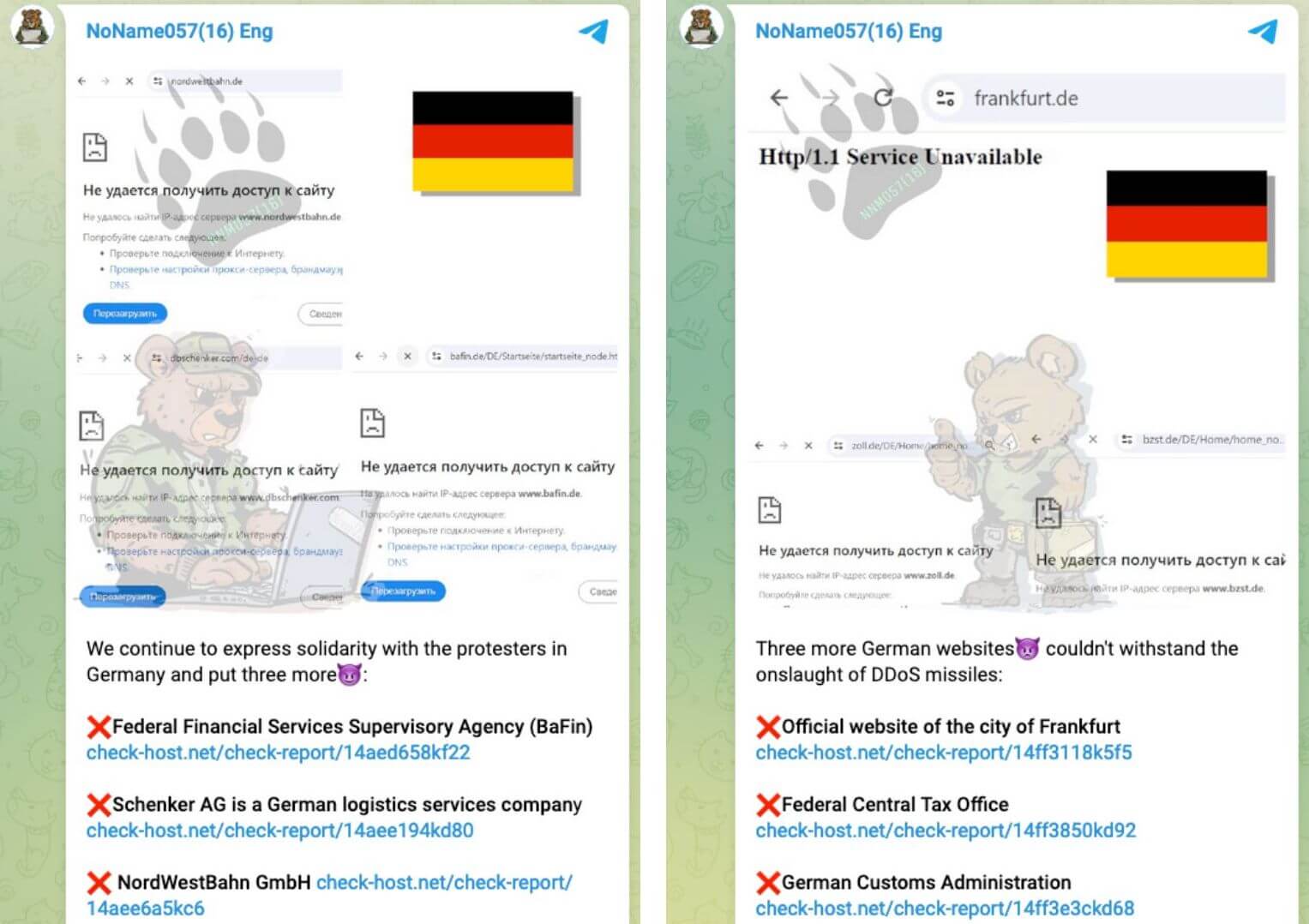
During attacks on Germany at the beginning of the year, the pro-Russian group boasted on Telegram that it had crippled the websites of the country’s parliament, the armed forces and the customs authority, among others. In response to a request for comment, the Federal Office for Information Security which is tasked with keeping the country safe from cyber attacks said it was aware of DDoS attacks against Germany attributed to NoName057(16).
Various Hacking Groups Use the Neculitis’ Servers
According to the Swiss cyber authority, the data traffic of NoName057(16)’s DDoS attacks originated from Russian IP addresses, networks of a company called Mirhosting – and from Stark Industries Solutions, the UK shell company of the Neculitis.
To this day, the programs used by the group to coordinate its DDoS attacks appear almost daily on the Neculitis’ servers, according to analysis by Spamhaus, a non-profit group that monitors malicious internet activity. Carel Bitter, a security researcher at Spamhaus, registered 48 so-called botnet control scripts from NoName057(16) over a period of two months in early 2024 – half of them on servers by Stark Industries Solutions. “That’s too much of a coincidence,” says Bitter. Ivan Neculiti didn’t respond to questions regarding these findings.
It is unlikely that the companies providing the servers are unaware of this activity. After all, the DDoS attacks by NoName057(16) are by no means the only cyber attacks to the benefit of Russia that have been carried out using the Neculitis’ infrastructure. They include attacks on the Ukrainian mobile phone provider Kyivstar and, according to reports by Recorded Future, attacks by a group called BlueCharlie, which carries out espionage against Ukraine and NATO members.
Hackers who are said to work directly for the Kremlin may also have used the brothers’ servers: according to a Ukrainian government report, Stark Industries Solutions’ infrastructure was used in a cyberattack on the Ukrainian news agency “Ukrinform” in January 2023. The infamous Sandworm hacking unit, which is said to be part of Russia’s GRU military intelligence service, were suspected to be behind the attack.
Disinformation backed by the Kremlin, DDoS and hacker attacks by pro-Russian actors – the accumulation of suspicious activity on the servers of the Neculitis raises questions about the brothers’ role in these aggressions. What do they know about what is happening on their devices? And what about the other companies involved?
Who Is in the Know?
The first step in curbing criminal or malicious internet activity is to report it to the hosting provider. It is assumed that the provider itself has been taken advantage of and they are given the opportunity to act. The reaction to such an abuse report is therefore also a measure of the hoster’s professionalism and reliability.
Ivan Neculiti had already earned a bad reputation in the industry with an earlier project. He “is infamous for owning web hosting companies used for malicious and illegal activities”, the IT security company Morphisec wrote in a 2022 report. Criminals had operated on his previous web hosting service Morenehost. At the time, Neculiti was still hiding the fact that he was behind the company. Morenehost was registered in the Seychelles – his ownership only became public following a data leak, the so-called Pandora Papers. Since then, he has been described in the industry as a so-called “bulletproof” hoster, meaning a provider that shields its clients from legal prosecution.
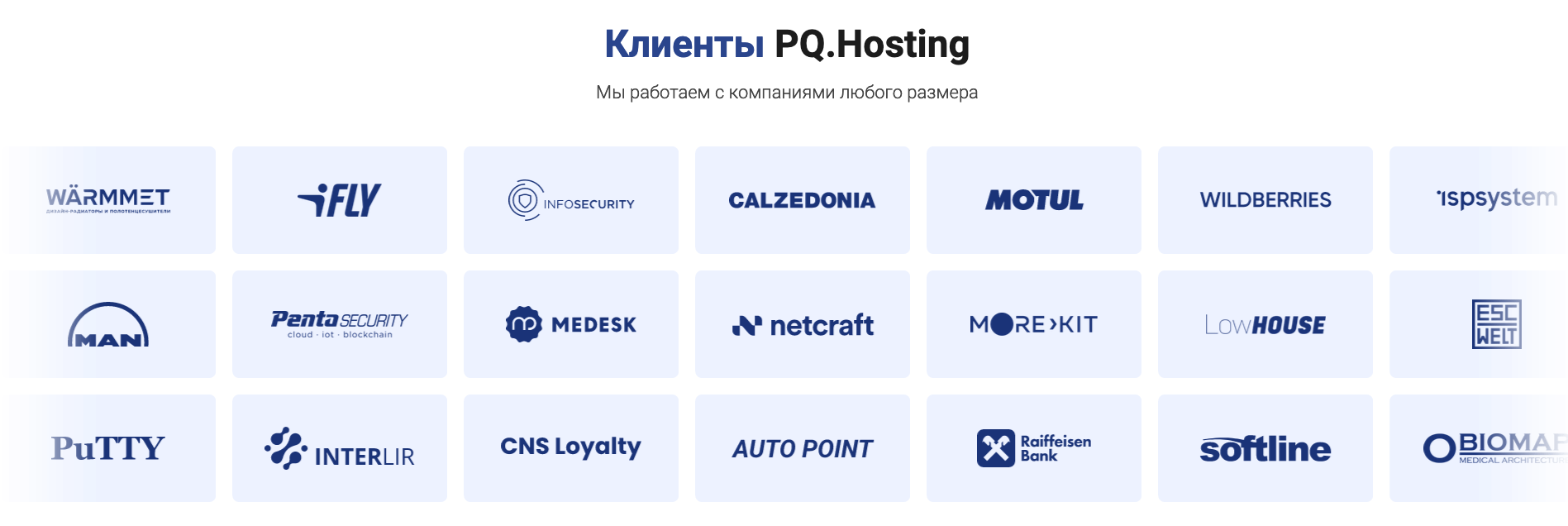
With PQ Hosting, Neculiti now presents himself as a serious businessman with a respectable company. On the website, PQ Hosting lists an impressive roster of clients, including companies from Europe and the United States. For example, the logos of Raiffeisen Bank or Munich-based truck maker MAN can be seen in the list. The two companies denied having a business relationship with PQ Hosting or Stark industries, however, adding that their logos had been used without permission. Following our reporting, PQ Hosting removed the entire client list from its website.
Either way, questionable activities continue to run via the Neculitis’ servers. In response to a request for comment by CORRECTIV, the Swiss Federal Office for Cybersecurity said that it had sent abuse reports “to some of the network operators involved” in the course of the DDoS attacks but didn’t receive any response. In an online forum a user wrote something similar – Stark Industries didn’t respond to an abuse report.
Ivan Neculiti denies these allegations: “We take all complaints from individuals, organizations, and government agencies, including law enforcement agencies of any country, seriously to combat illegal activities.” In response to questions about specific incidents, he replied in general terms that using their servers for attacks and other illegal activities was “absolutely not allowed.”
Hosting companies are the lowest link in a chain of service providers that connect their customers to the internet. They often act as so-called resellers, renting servers from larger companies and passing them on. In other cases, they own their own technology which they install in large and well-connected data centers. It is also common for tenants in a data center to share data traffic or tap into the capacities of others. Sometimes there are a whole series of such resellers between the customer and the data center.
“It’s really easy to hide behind all these layers,” said Carel Bitter from Spamhaus. For those who provide the physical infrastructure, it is difficult to know who is using it in the end. “You’re renting the rack [a cabinet used in a datacenter to house and organize servers] and you don’t know what’s in that,” he said. In turn, the person renting out the servers doesn’t know what’s happening on the individual VPS sections of a server, either, he adds.
The Neculitis Use a Data Center in the Netherlands
The servers in the Netherlands which the Neculitis provide to their customers are located in a data center by a Dutch company named Serverius. Neither Serverius nor the Neculitis wanted to disclose the details of their contractual relationship. It remains unclear how many resellers are involved and what role the company Mirhosting plays, which is also mentioned in the Swiss cyber authority’s report on NoName057(16). However, the links between the individual companies and individuals are striking.
The general manager of Mirhosting, Andrey Nesterenko, came to the attention of experts back in 2008, during Russia’s war against Georgia. Back then, his IT projects were involved in a pro-Russian cyber attack against Georgia, according to different research reports. This didn’t prevent Serverius from employing Nesterenko as a sales representative between 2014 and 2016. Nesterenko’s company Mirhosting is also connecting to the internet via Serverius and its infrastructure has reportedly also been used in pro-Russian hacking activities in recent years.
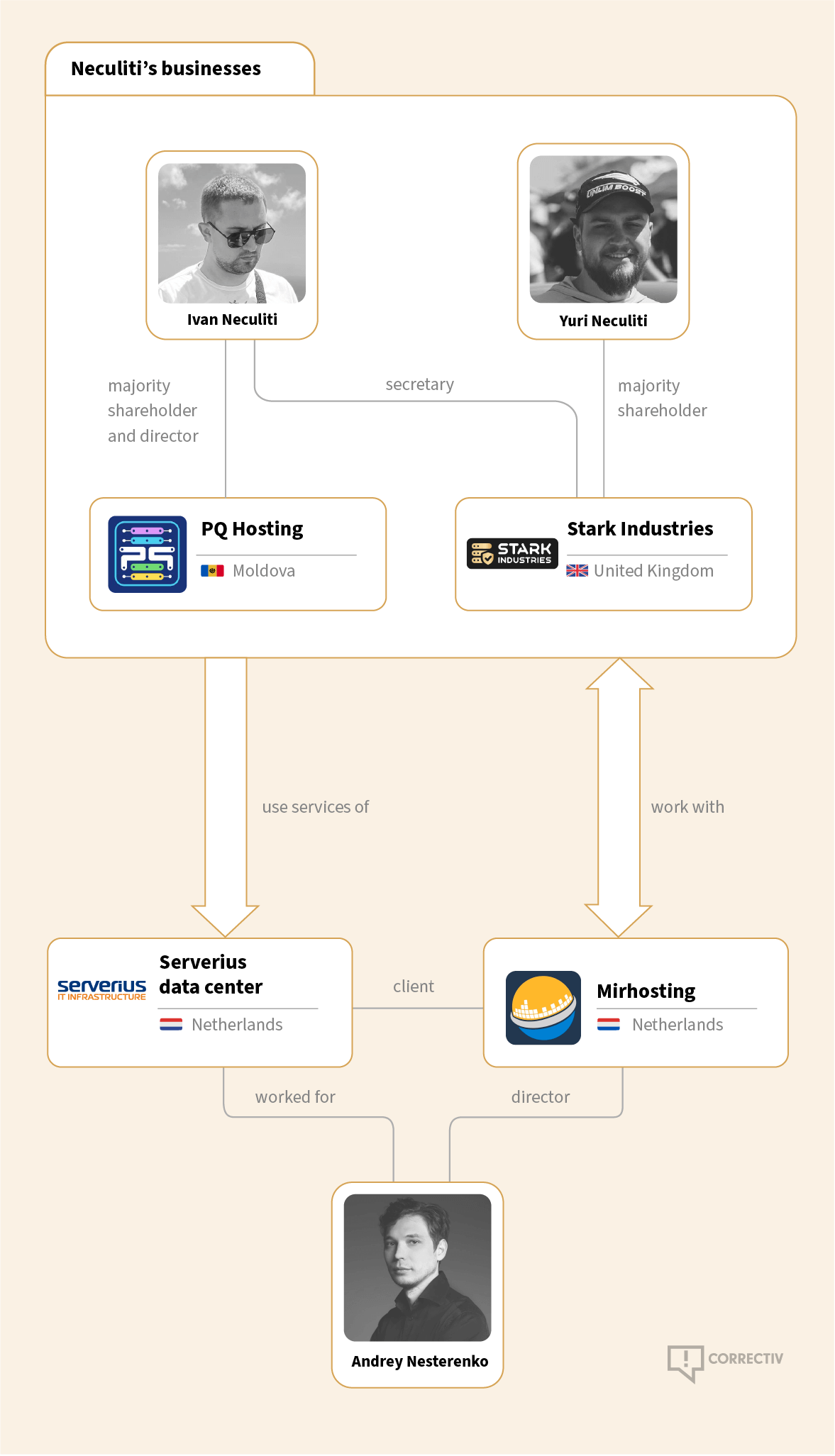
In the data center, Mirhosting shares the data traffic of Neculiti’s customers as one of several upstream companies (“peers”). Neculiti, in turn, says in a promotional interview in 2022 that his servers were connected by Serverius free of charge – sending his regards to Sergey Petukhin, head of network infrastructure at Serverius.
“We do not own these servers and have no control over what our customers store on them or the traffic they send to or from our facilities,” Maria Sundvall, chief executive of Serverius, said in an emailed response. Whenever the company identified any suspicious activity in the past, it „acted swiftly,“ she said, adding that „any customer identified as being on a sanctions list will have their contract terminated immediately.“
Nesterenko said that he had no information about the hacking attack on Georgia in 2008, adding that his company takes „immediate action against any abuse.“ He confirmed that Stark Industries Solutions is a customer of Mirhosting. Asked about the activities of NoName057(16), Nesterenko said that they were “now” working with the Dutch government and referred to the cyber police, declining to provide detailed information. The Dutch cyber police declined to comment.

The EU’s Toothless Sanctions
The EU sanctions on the Russian companies and individuals behind the RRN disinformation websites prohibit European companies from doing business with them. While Stark Industries Solutions as a British company and PQ Hosting as a Moldovan company are not subject to EU legislation, Serverius and Mirhosting as Dutch companies are.
According to David Rösch, sanctions expert at the law firm Noerr, the ban applies to both the direct and indirect provision of funds and economic resources. “It also applies if I provide web hosting services to third parties that subsequently benefit the sanctioned persons,” he said, adding that a prerequisite is that the listed persons can potentially earn money with the site.
When asked, the Dutch Ministry of Foreign Affairs, which is responsible for enforcing sanctions, confirmed this legal assessment but declined to comment on the specific case.
“The enforcement of sanctions must be a natural part of our defense capabilities,” said Sergey Lagodinsky, a leading candidate for Germany’s Green party in the European elections this June. The immediate threat to the EU is not a conventional attack, but an attack using means such as disinformation, he said. It is therefore necessary to clarify how sanctions can be enforced politically and, if necessary, legally, he added. “It is the responsibility of the new Commission to ensure that sanctions-related activities are carried out in a more centralized and coordinated manner,” he said.
Foreign influence campaigns such as “doppelganger” pose “a threat to our liberal democracy and are particularly dangerous in the run-up to elections,” said CDU member of parliament Roderich Kiesewetter. “The fact that sites like this can still be accessed weakens societal resilience.”
Kiesewetter is part of a Bundestag committee that monitors the work of the German intelligence services. In a rare public statement in mid-March, the auditors warned of Russian influence and called for Germany to “position itself much more robustly, resiliently and defensively” in the future. According to the report, the Russian toolbox also includes “extensive disinformation campaigns” and cyber attacks.
“The aim of such attacks is primarily to spread mistrust of democracy and state institutions,” said Kiesewetter. “If the perpetrators are known, it is imperative that these attacks are stopped.” However, sanctions are only effective if the member states enforce and implement them accordingly, he added.
Meanwhile, the Neculitis are continuing to work on their hosting empire. The brothers are now planning to open their own data center, according to an announcement on their website – the location, it said, remains a secret for now.
Editing: Alice Echtermann, Anette Dowideit
Design: Ahmed Mounir
English translation: Max Bernhard, Sophie Timmermann




